
In today’s digitally dominated world, the need for rock-solid security measures has never been more crucial. This blog post delves into the essential role of Identity Governance in fortifying digital security. We’ll highlight why it’s a game-changer for safeguarding sensitive information and maintaining the integrity of organizational assets.
As businesses increasingly rely on interconnected digital platforms, the risk landscape has expanded exponentially. Cyber threats, data breaches, and unauthorized access are not just buzzwords; they are real challenges that organizations face daily. Against this backdrop, Identity Governance emerges not only as a solution but as a proactive strategy, empowering organizations to stay one step ahead of potential threats. It’s not just about securing data; it’s about creating a digital environment where trust, compliance, and operational efficiency coexist harmoniously. Let’s delve into the layers of Identity Governance and unveil the strategies that can turn your digital realm into an impenetrable fortress.
The Customer-Centric Shift
What’s Identity Governance, Anyway?
Identity Governance (IG) is like the superhero of managing digital identities. It’s not just about handling user accounts; it’s about overseeing roles, permissions, and activities within a company’s digital space. Think of it as your digital bouncer, making sure the right people have access to the right stuff at the right time.
Imagine your company’s digital environment as a bustling party. You’ve got guests (users), each with their unique needs and reasons for being there. Identity Governance steps in as the vigilant bouncer, checking guest lists (access permissions) to ensure only the invited guests get through the door. It’s not just about granting entry; it’s about ensuring everyone plays by the rules and doesn’t overstay their welcome.
Just like a superhero, IG operates behind the scenes, silently but powerfully safeguarding your digital assets. It’s the unsung hero that prevents chaos and secures the perimeter, allowing your organization to focus on innovation and growth without constantly looking over its digital shoulder.
Identity Governance (IG) is the superhero of managing digital identities, ensuring the right people have access to the right stuff at the right time – a silent guardian in the ever-evolving digital landscape.
Why It Matters:
In the dynamic landscape of digital operations, Identity Governance (IG) emerges as a linchpin, addressing critical aspects that go beyond conventional access management. Let’s delve into why IG matters and how it reshapes the digital narrative:
1. Risk Mitigation:
IG acts as a proactive shield, akin to having a digital bouncer at the entrance of your digital realm. It meticulously scrutinizes access requests, cutting the risk of unauthorized entry and potential data breaches. Picture it as the vigilant guardian that keeps the bad actors out, ensuring your organization’s sensitive information remains secure.
2. Compliance Adherence:
With the regulatory landscape becoming increasingly complex, IG serves as your digital compliance partner. Rules and regulations such as GDPR and HIPAA are not just checkboxes; they are integral to maintaining trust and credibility. IG ensures your organization stays on the right side of the law, providing a structured approach to compliance and minimizing the risk of legal pitfalls.
3. Operational Efficiency:
IG doesn’t stop at keeping things secure; it actively contributes to making your digital life easier. By managing user access and permissions with precision, IG reduces errors, streamlines workflows, and ensures everyone in your digital ecosystem has the tools they need. It’s not just a security measure; it’s a catalyst for operational efficiency, empowering your team to focus on innovation and productivity without being bogged down by access-related complexities.
In essence, Identity Governance transcends traditional access management; it’s a strategic asset that aligns security, compliance, and operational efficiency, creating a robust foundation for your organization’s digital success.
Key Components of Identity Governance
In the intricate realm of Identity Governance (IG), various components seamlessly come together to weave a robust framework that goes beyond traditional access management. Let’s unravel the key components that form the backbone of IG and understand how they collectively contribute to a secure and efficient digital ecosystem.
1. Identity Lifecycle Management:
Registration and Onboarding: In the digital narrative, smooth onboarding is the opening act. IG ensures that new members seamlessly get what they need without unnecessary hassles, setting the stage for a positive digital experience from the start.
Role Assignment: Think of the digital playground as a well-scripted play. Clearly defined roles, managed by IG, ensure that everyone knows who’s who and what responsibilities they hold, preventing any digital chaos.
Modification and Updates: As the script of your organization’s digital narrative evolves, IG steps in to ensure that everyone’s access keeps pace with the changes. It’s the director behind the scenes, orchestrating seamless adjustments to roles and permissions.
Deactivation and Offboarding: When the final curtain falls for an employee, IG ensures a smooth exit. It deactivates access promptly, ensuring departing individuals don’t take their digital access privileges with them, preventing potential security breaches.
2. Access Management:
Authentication: IG implements strong authentication methods that act as the gatekeepers to your digital domain. It’s like having a vigilant guard at the entrance, ensuring only the right people get through.
Authorization: Think of IG as the rulebook for your digital space. It sets clear rules and regulations, ensuring that everyone accesses only what they’re authorized to. It’s about maintaining order in the digital realm.
Single Sign-On (SSO): Simplifying the digital experience, IG introduces the concept of a unified key – one password to rule them all. This not only enhances security but also makes life simpler for everyone navigating the digital landscape.
3. Policy Enforcement:
Establishing Access Policies: IG lays down the ground rules for your digital arena. It’s like the constitution, defining the principles that govern access and maintain a secure environment.
Continuous Monitoring: Ever-vigilant, IG keeps an eye on the digital pulse. Continuous monitoring allows for the early detection of anything unusual, ensuring potential threats are identified and addressed promptly.
Automated Policy Enforcement: IG leverages automation as its digital enforcer. Letting automation handle the heavy lifting ensures consistent adherence to policies, reducing the margin for human error and ensuring everyone follows the rules without fail.
These components collectively form the dynamic and adaptive structure of Identity Governance, turning it into more than just a gatekeeper; it’s the architect of a secure, compliant, and well-orchestrated digital symphony.
Benefits of Implementing Identity Governance
In the ever-evolving landscape of digital security, implementing Identity Governance (IG) isn’t just a strategic choice; it’s a transformative step toward fortifying your digital frontiers. Let’s explore the myriad benefits that come with the implementation of IG, transcending mere access management to shape a resilient and user-friendly digital environment.
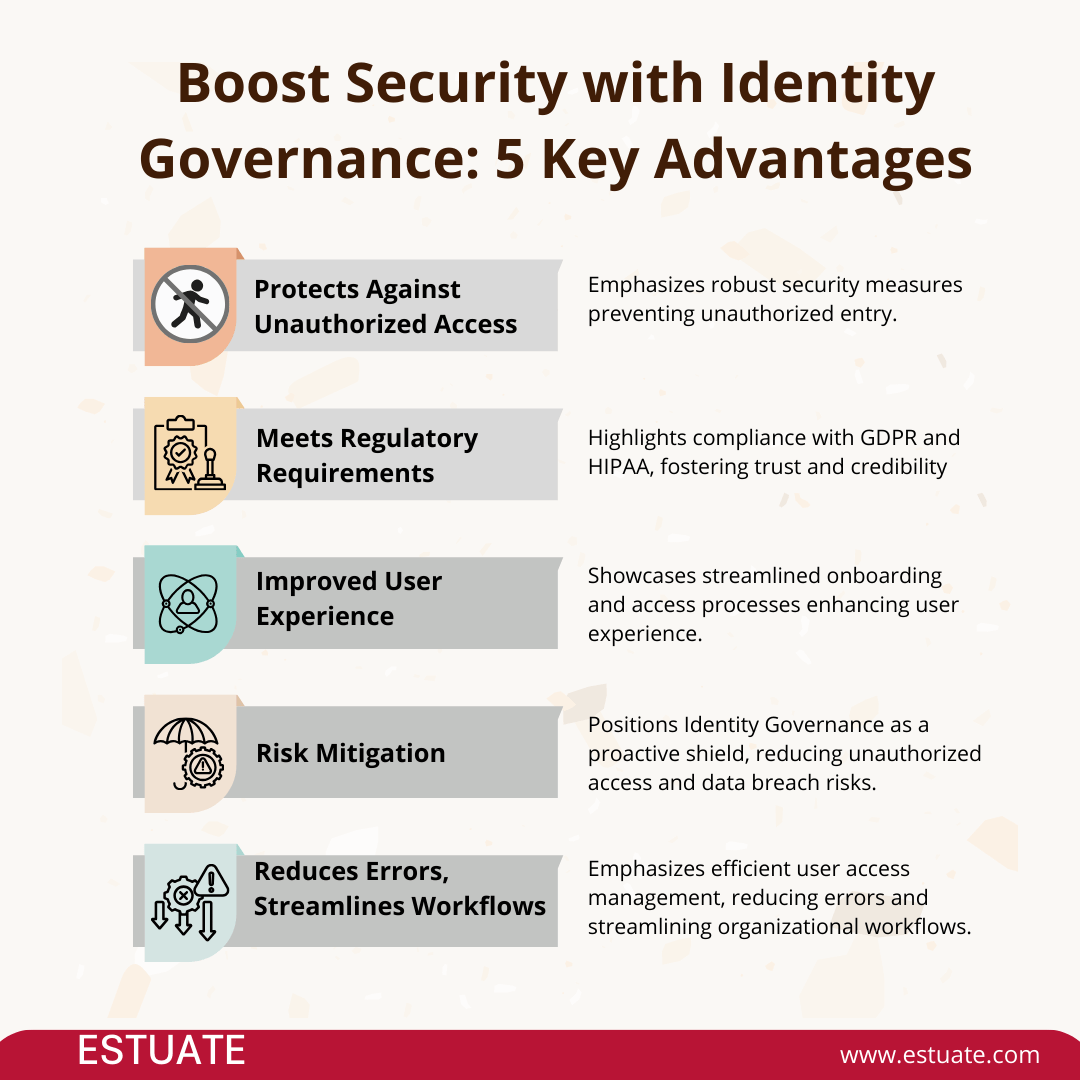
The 5 key advantages of boosting security with identity governance
1. Enhanced Security:
Protecting against Unauthorized Access: IG steps into the role of a digital gatekeeper, ensuring only authorized individuals gain access to your organization’s digital assets. Think of it as the vigilant guardian at the entrance, keeping the bad actors out and safeguarding sensitive information from unauthorized hands.
Detecting and Responding to Anomalies: Beyond just fortifying the gates, IG keeps a watchful eye on the digital landscape. It actively detects unusual patterns and behaviors, enabling swift responses to potential security threats before they escalate into problems.
2. Compliance and Audit Trail:
Meeting Regulatory Requirements:In the complex terrain of digital regulations, IG serves as your compliance companion. By maintaining a meticulous record of user activities, it ensures your organization stays on the right side of the law. It’s not just about following regulations; it’s about creating a secure foundation for trust and credibility.
Providing a Transparent Audit Trail: Imagine your organization’s digital activities as an open book. IG ensures transparency by providing a comprehensive audit trail, allowing you to know exactly who did what in your digital realm. This transparency not only aids in compliance audits but also contributes to a proactive security posture.
3. Improved User Experience:
Efficient Access Provisioning:IG streamlines the journey from onboarding to daily operations. It ensures that individuals get precisely what they need, precisely when they need it. No unnecessary hurdles, no delays – just efficient access provisioning that enhances the overall user experience.
Simplified Authentication Processes: Keeping it simple is key to a positive user experience. IG introduces easy and effective authentication processes, making it seamless for users to navigate the digital landscape securely. It’s about striking the right balance between security and user convenience.
Implementing Identity Governance isn’t just about securing access; it’s a strategic move that redefines the way your organization interacts with its digital ecosystem. It’s a multifaceted solution that not only strengthens security but also fosters compliance, transparency, and user satisfaction.
Challenges and Best Practices
Navigating the landscape of Identity Governance (IG) isn’t without its challenges, but with strategic best practices, organizations can overcome hurdles and build a resilient digital infrastructure. Let’s explore the challenges that often accompany IG implementation and the best practices that pave the way for a secure and streamlined digital environment.
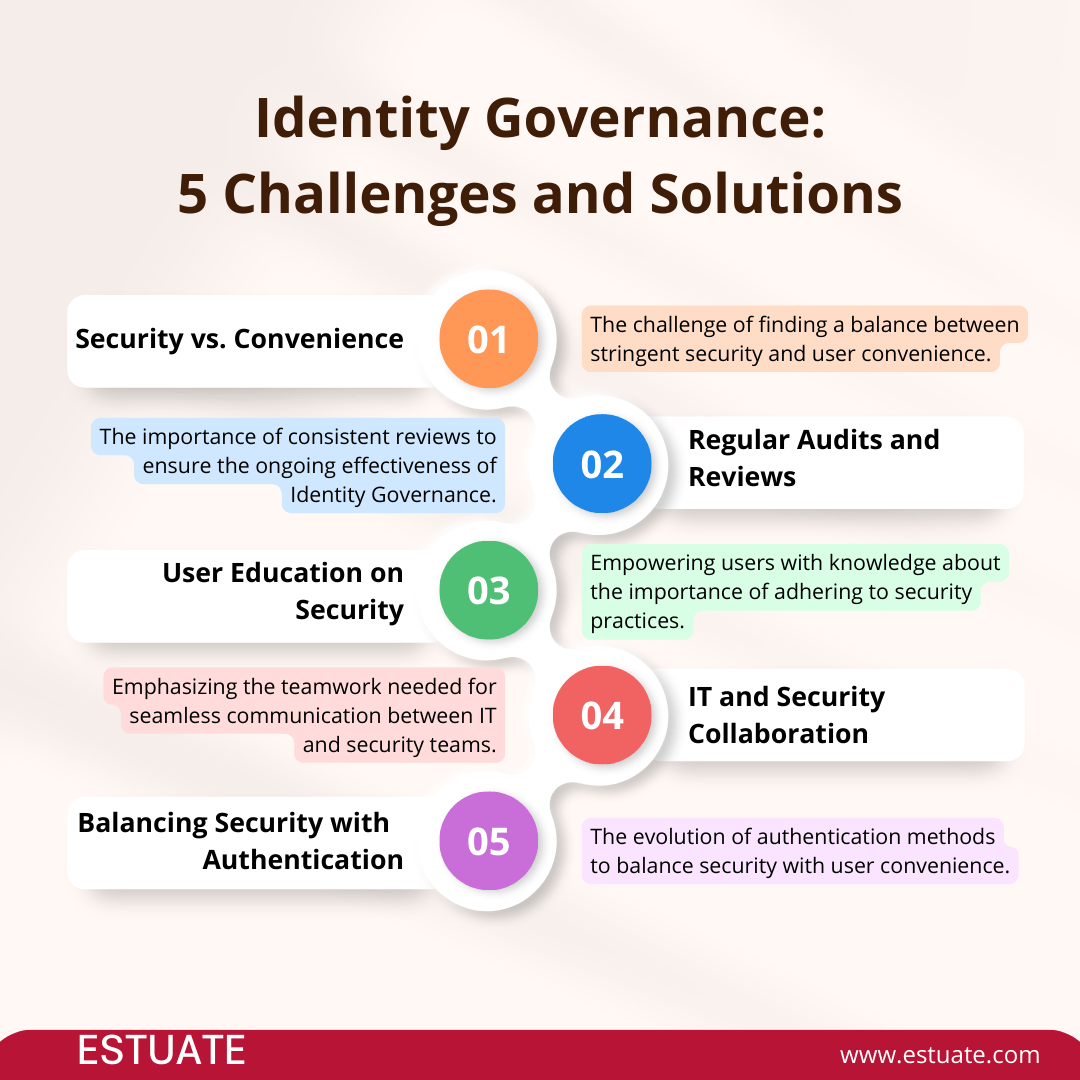
5 challenges and solutions for identity governance in visuals.
1. Challenges in Identity Governance
Balancing Security and User Convenience: Picture it as a tightrope walk – ensuring stringent security measures without making it a hassle for users. The challenge lies in finding that sweet spot where security remains robust, and user experience remains seamless.
Managing Identities in Dynamic Environments: In the dynamic dance of organizational changes, IG needs to keep up. Regular updates and checks are essential to ensuring that IG adapts swiftly to evolving identities and permissions, staying on its toes to maintain effectiveness.
2. Best Practices
Regular Audits and Reviews: Keep things fresh and effective through regular audits and reviews. This ensures that IG remains aligned with organizational objectives, adapts to changes, and continues to be a proactive guardian of digital access.
User Education on Security Practices: A little education goes a long way in fortifying the human element of security. Ensure everyone in the digital landscape understands the importance of playing by the rules. Educated users are empowered users, contributing to a stronger security posture.
Collaboration between IT and Security Teams:Teamwork makes the dream work. Establish seamless communication and collaboration between IT and security teams. This ensures that IG strategies align with broader organizational security objectives, creating a united front against potential threats.
Facing challenges head-on with these best practices transforms Identity Governance from a mere gatekeeper into a proactive and adaptive force in the digital realm.
In this ever-evolving digital landscape, Identity Governance stands as your digital superhero, defending against cyber threats. By managing user identities and access with finesse, organizations not only strengthen their defenses but also create a secure and compliant environment. Embracing Identity Governance isn’t just a smart move; it’s a must in the age of digital interconnectedness.
Estuate’s Expertise in Identity Governance and Security Solutions
At Estuate, we bring a wealth of expertise to the forefront of Identity Governance and Security Solutions. With a commitment to delivering cutting-edge technologies, our solutions are designed to empower organizations in tackling the complexities of digital security. From implementing robust Identity and Access Management strategies to integrating advanced Security Solutions, we tailor our offerings to meet the unique challenges of the modern business landscape.
At Estuate, we don’t just manage identities; we orchestrate a secure and efficient digital symphony.
Contact Us to Fortify Your Digital Frontiers
Ready to elevate your organization’s digital security to new heights? Contact Estuate today to explore how our expertise in Identity Governance and Security Solutions can become the cornerstone of your cybersecurity strategy. Reach out to us at contatcus@estuate.com or visit us at www.estuate.com to learn more about our solutions and how we can fortify your digital landscape. Your digital fortification starts here.